Table of Contents
KyberSwap, a decentralized exchange (DEX), became the latest victim of a sophisticated cyber heist, losing over $48 million across six different blockchain networks. The modus operandi? A flash loan attack, a prevalent yet potent threat in the decentralized finance (DeFi) space.
The assault was not just a display of technical prowess but also a psychological warfare, as the hacker left a trail of on-chain taunts, a growing trend in DeFi exploits.
What Are Flash Loan Attacks?
Flash loans are a relatively new form of uncollateralized lending, which, contrary to traditional loans, do not require collateral. They are enforced by smart contracts and allow borrowers to take out massive loans, provided they can repay within the same transaction.
Flash loan attacks are the most common types of attacks in the DeFi sector due to their low-risk, high-reward nature. They require minimal resources: just a computer, an internet connection, and ingenuity, making them relatively easy to execute and hard to trace. The anonymity and permissionless nature of blockchain networks further augment the difficulty in tracking these cybercriminals.
How the Kyber Exploit Happened
The exploit was a highly sophisticated and carefully engineered attack on KyberSwap's implementation of concentrated liquidity. It stands out as one of the most complex smart contract exploits observed to date. Here's a breakdown of how the exploit unfolded, as explained by Twitter/X user Doug Colkitt.
1/ Finished a preliminary deep dive into the Kyber exploit, and think I now have a pretty good understanding of what happened.
— Doug Colkitt (@0xdoug) November 23, 2023
This is easily the most complex and carefully engineered smart contract exploit I've ever seen...
- Initial Flash Loan and Price Manipulation: The attacker started by taking a flash loan of 10,000 wstETH (worth about $23 million). They then swapped 2,800 wstETH ($6 million) into the ETH/wstETH pool, drastically pushing the price from 1.05 ETH to 0.0000152 ETH. This step was not to manipulate an oracle but to move the pool's price to a part of the liquidity curve where there was no existing liquidity, creating a 'fresh canvas' for the exploit.
- Manipulating Liquidity: The attacker minted 3.4 wstETH of liquidity in a specific price range and then burned a portion of it (0.56 wstETH). This step was probably to align subsequent numerical calculations precisely.
- Executing Swaps for the Infinite Money Glitch: The attacker executed two critical swaps around this manipulated price. The first swap involved selling 1,056 wstETH for 0.0157 ETH, which pushed the price down to 0.0000146 ETH. The second swap was in the opposite direction, where the attacker bought 3,911 wstETH from the pool for 0.06 ETH, pushing the price up to 0.00001637 ETH. These swaps resulted in the attacker receiving more wstETH than they initially sold, effectively draining the pool.
- Exploiting a Flaw in Liquidity Management: The core of the exploit lay in manipulating how liquidity was managed within the pool. Normally, the
updateLiquidityAndCrossTickfunction in KyberSwap is called when the price crosses certain boundaries (ticks) in the pool, adding or removing liquidity from the pool's curve. However, during the first swap, this function was never invoked, even though it should have been, allowing the attacker to trick the pool into thinking it had more liquidity than it actually did. - Technical Manipulation of Swap Steps: The exploit leveraged a technicality in how swaps are calculated. KyberSwap checks if the ending price of a swap step is the same as the next tick price. If it isn't, it assumes the swap didn't reach the tick boundary, and the
updateLiquidityfunction isn't called. The attacker precisely engineered their swaps so that the ending price was just beyond the tick boundary, bypassing the call toupdateLiquidity. - A Difference in Arithmetic Calculations: The exploit was facilitated by a slight difference in how KyberSwap's smart contracts calculated the upper limit of a swap quantity and the resultant price change. This difference allowed the attacker to manipulate the swap steps to create the illusion of additional liquidity in the pool.
Why Are Flash Loan Attacks Rising?
Flash loans are a relatively new form of uncollateralized lending, which, contrary to traditional loans, do not require collateral. They are enforced by smart contracts and allow borrowers to take out massive loans, provided they can repay within the same transaction.
Flash loan attacks are the most common types of attacks in the DeFi sector due to their low-risk, high-reward nature. They require minimal resources: just a computer, an internet connection, and ingenuity, making them relatively easy to execute and hard to trace. The anonymity and permissionless nature of blockchain networks further augment the difficulty in tracking these cybercriminals.
KyberSwap's Predicament
The losses were distributed across several blockchain networks, with over $20 million taken from Arbitrum, $15 million from Optimism, $7.5 million from Ethereum, and smaller amounts from Polygon, Base, and Avalanche.

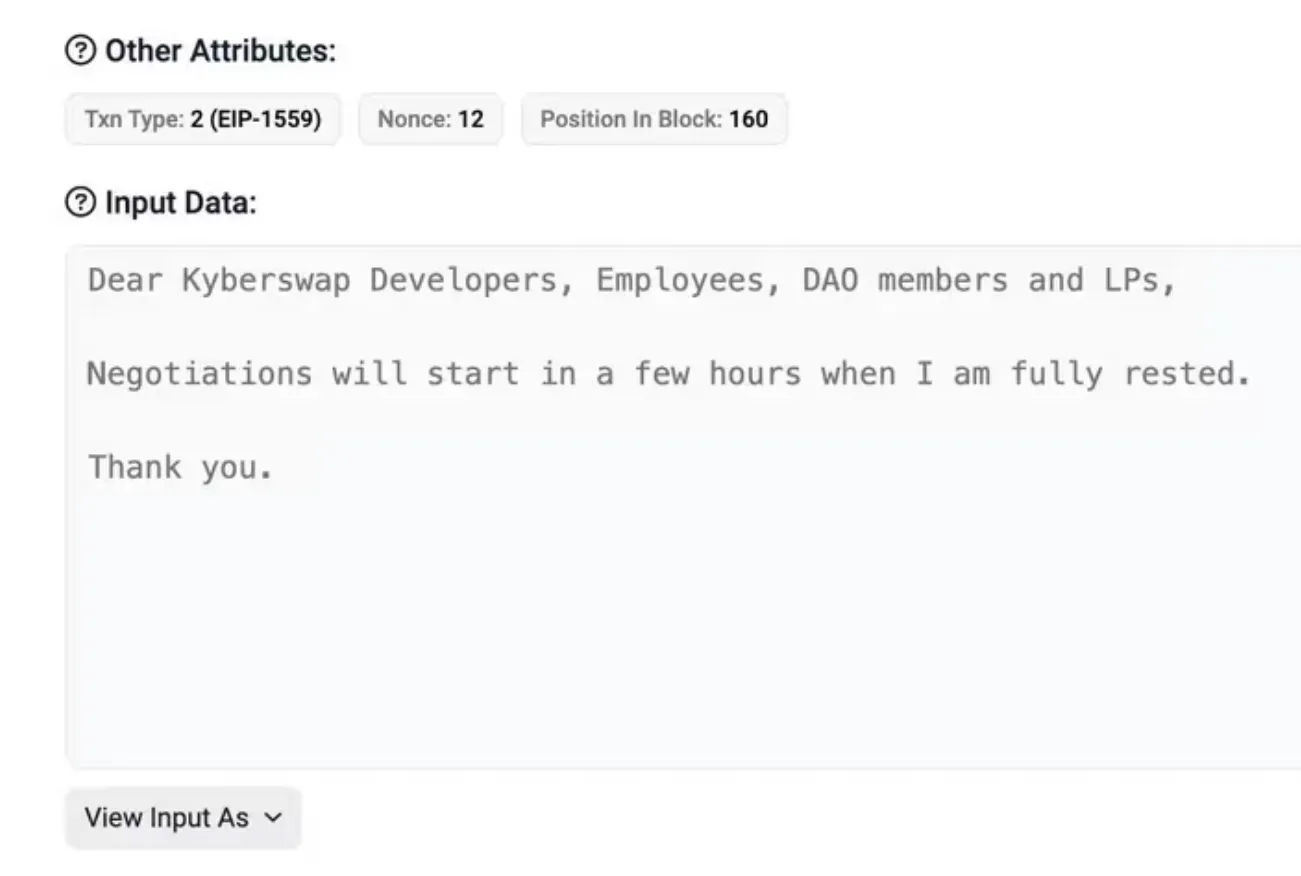
Interestingly, the hacker left a trail of on-chain comments throughout the attack, demonstrating a certain level of flair and possibly even taunting their victims. This behavior included sending a notable amount of stolen funds to an address linked to a previous major hack.
Following the attack, the hacker indicated a willingness to negotiate, suggesting that they might be open to returning the stolen funds or discussing terms. KyberSwap administrators advised users to withdraw their funds as a precaution, and an investigation into the incident is ongoing.
The KyberSwap exploit – not the first, and certainly not the last of this kind in the DeFi space – serves as another expensive lesson for the DeFi community. It underscores the importance of ongoing vigilance, continuous improvement in security protocols, and perhaps a rethinking of how DeFi platforms can safeguard against such sophisticated attacks.
As the industry continues to grow, so does the need for more resilient and secure systems to protect the assets and trust of its users.